In 2025, the human element is implicated in roughly 60% of breaches, according to Verizon’s latest Data Breach Investigations Report (DBIR). Credential abuse remains the most common attack vector, while ransomware has surged — present in 44% of breaches, up from 32% the year before. Alarmingly, small and mid-sized businesses (SMBs) were hit hardest, with ransomware playing a role in 88% of their breaches. These numbers highlight what’s at stake: authentication isn’t just a technical safeguard — it’s central to business resilience and trust.
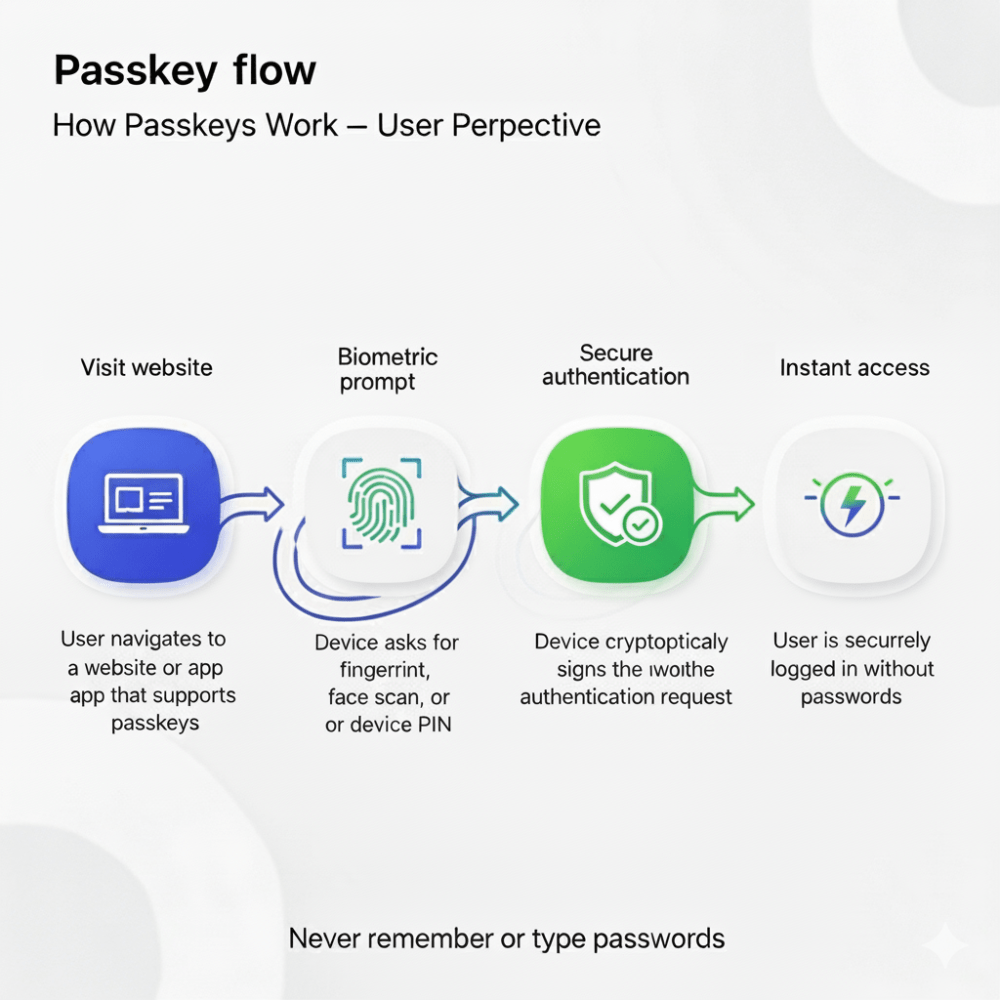
1. The Passwordless Revolution: Biometrics and Passkeys
Passwords are rapidly fading into the background. Fingerprints, facial scans, and passkeys — device-bound credentials backed by FIDO2 standards — are making authentication seamless.
- Example: Picture this: a leading bank deploys a biometric system and subsequently reduces its volume of password-related support requests by more than 80%.
- User Benefit: Passwordless logins cut login time nearly in half while reducing password fatigue.
- Statistic: According to the RSA ID IQ Report 2025, 61% of organizations plan to roll out passwordless authentication within a year.
- Challenge: Integrating these systems with legacy infrastructure is complex. Many older platforms rely on outdated hashing schemes, making user migration and recovery workflows a sticking point (RF Ideas Report).
2. AI-Powered Authentication & Fraud Detection

Artificial intelligence now underpins identity verification by analyzing login behavior, device fingerprints, and even liveness detection.
- Example: Global fintech firms use AI-driven fraud detection to stop synthetic identity fraud before it reaches the transaction stage.
- Challenge: Overly sensitive algorithms can trigger false positives, creating friction for legitimate users. Fine-tuning is critical.
3. Behavioral Biometrics: Security That Blends In
Keystroke rhythms, touchscreen gestures, mouse flow, and even walking patterns can uniquely identify users. This continuous, invisible authentication builds security without interrupting the user journey.
- Example: Large e-commerce platforms detect suspicious behavior in real time, flagging fraud while minimizing checkout disruption.
- Challenge: Models must be trained across diverse datasets to avoid bias, especially when users switch between mobile and desktop.
4. Regulatory Pressure: Compliance and Privacy
Frameworks like GDPR, CCPA, and BIPA dictate how biometric data must be collected, stored, and shared. The cost of non-compliance is steep.
- Statistic: GDPR fines totaled €1.2 billion in 2024, with TikTok hit by a €530 million penalty in 2025 alone.
- Challenge: Organizations must ensure privacy-by-design, with clear consent and transparency baked into authentication flows.
5. Decentralized Identity: A User-Centric Model

Decentralized identity (DID) shifts control away from centralized databases, letting users share only the information required.
- Example: Estonia’s e-Identity system offers a secure, interoperable way for citizens to access services.
- Challenge: Interoperability remains limited. Without common standards, adoption may remain fragmented.
6. Future Frontiers: IoT, AR/VR, and Quantum Readiness
As connected cars, AR/VR headsets, and smart home ecosystems expand, new authentication methods — like voiceprints and gaze recognition — must be both secure and intuitive.
- Quantum Threat: Quantum computers could one day break RSA and ECC encryption, undermining today’s internet security.
- Response: The NIST Post-Quantum Cryptography project is developing standards like lattice-based cryptography to future-proof digital security.
7. Integration and Transition Challenges
- Legacy migration: Passwordless adoption often stalls on outdated recovery processes and resistance from both IT teams and users.
- Quantum-safe preparation: Smart organizations are beginning pilot projects with post-quantum algorithms, ensuring smoother adoption later.
Summary Table: Trends, Benefits, Trade-offs
| Trend | Key Benefit | Core Challenge |
|---|---|---|
| Passwordless (Biometrics) | Fast, secure, user-friendly | Legacy integration, recovery workflows |
| AI & Adaptive Security | Proactive fraud prevention | False positives, fine-tuning required |
| Behavioral Biometrics | Continuous, invisible authentication | Bias in models, device variability |
| Regulatory Compliance | Avoids fines, builds user trust | Complex global requirements |
| Decentralized Identity (DID) | User control, privacy-friendly | Interoperability and adoption hurdles |
| IoT / AR/VR Authentication | Fits new tech ecosystems | Hardware limitations, UX challenges |
| Quantum-Safe Encryption | Future-proof security | Early adoption costs, performance trade-offs |

Conclusion: Build Trust Through Authentication
Authentication has transformed from a necessary friction into the invisible fabric of digital trust. From biometrics and AI to decentralized identity and quantum-safe cryptography, forward-thinking businesses must prepare today to remain secure tomorrow.
The future of authentication will define the next generation of digital experiences. The question is: Is your organization ready to lead the change?
ℹ️ Practical Tips for Professionals
Large Enterprises
- Roll out passwordless in phases: Start with internal teams before scaling.
- Adopt adaptive MFA: Trigger additional checks only for high-risk logins.
- Audit compliance: Map identity data flows to align with global privacy laws.
- Begin quantum readiness: Pilot DID wallets and track NIST post-quantum standards.
Startups & Cloud-Natives
- Use turnkey identity services: Cloud providers simplify passwordless adoption.
- Treat MFA as core protection: Implement authenticator apps across systems.
- Train staff on phishing: Human error remains the #1 breach cause.
Consumers & Small Business Owners
- Enable MFA everywhere: Email, banking, and e-commerce logins especially.
- Spot phishing attempts: Check links, avoid unsolicited password resets.
- Use a password manager: Strong, unique credentials reduce account compromise.












