Have you ever wondered what would happen if someone outside your company got into one of your top-level accounts? The damage could be severe — lost data, stolen credentials, or even complete control over your network. As more businesses rely on digital tools, protecting these powerful accounts has never been more important. Privileged accounts — like those belonging to system administrators or executives — hold the keys to your organization’s most sensitive assets. If these fall into the wrong hands, the consequences can be devastating.
In this blog, we will share clear and actionable steps you can take to secure your organization’s most powerful accounts and keep your data safe.
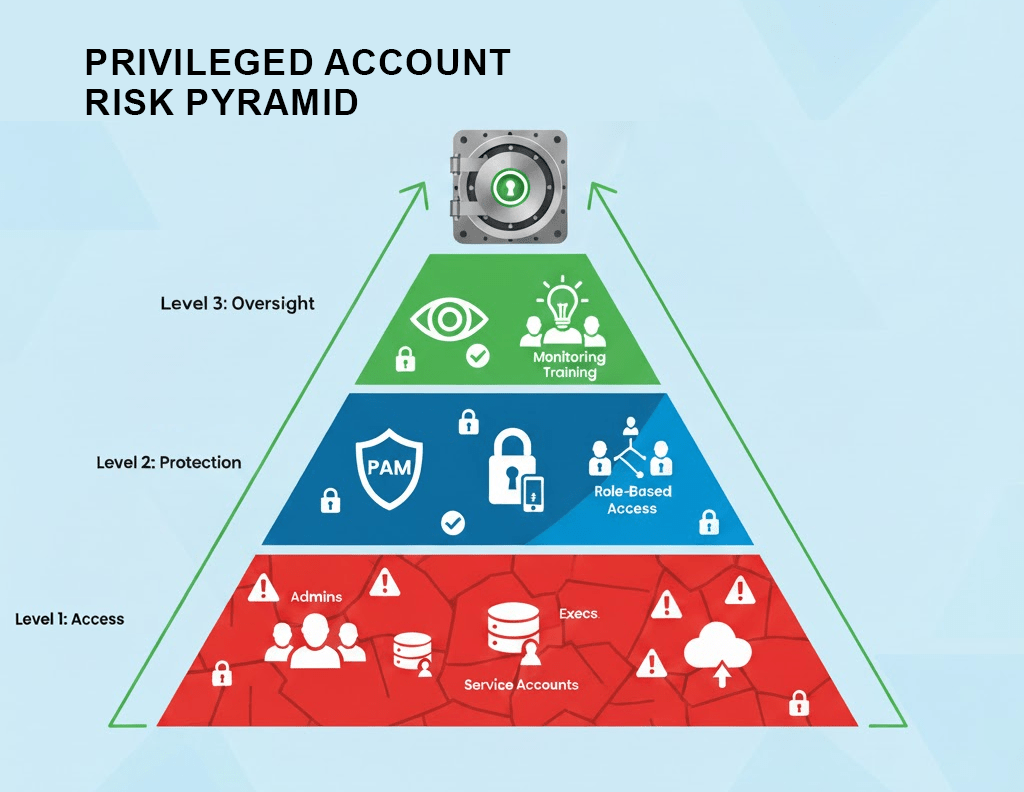
Identify and Classify Privileged Accounts
The first step to protecting your high-level accounts is figuring out which ones need extra attention. Start by identifying all accounts that have elevated access, such as IT admins, finance officers, and senior executives. Don’t forget service accounts or automated processes that also carry high privileges. These are often overlooked and can become entry points for attackers if left unmanaged.
Once you identify these accounts, classify them based on risk. Some accounts might have access to everything, while others may only have limited power. Grouping accounts this way helps prioritize which ones need tighter controls. You’ll also avoid treating all accounts the same, which saves time and resources. A good classification strategy leads to smarter, more targeted protection.
Adopt a Privileged Access Management (PAM) Strategy
After identifying and classifying accounts, the next logical step is setting up a system to manage them. A Privileged Access Management strategy helps you control who gets access to what and when. Instead of letting users log in freely with admin rights, PAM tools require them to go through strict authentication checks. These solutions limit exposure by granting temporary access only when necessary.
A good PAM solution also logs user activity, so you can see who did what and when. This is helpful for audits and spotting suspicious behavior. These tools offer centralized control over privileged accounts, with automated approval workflows and detailed reporting. This makes it easier to reduce risk while staying compliant with internal and external security rules.
Limit Access Based on Role and Need
Granting broad access to everyone is one of the easiest ways to increase your risk. Instead, follow the principle of least privilege. This means each user only gets the access they need to do their job, nothing more. For example, a customer support agent shouldn’t have access to your company’s financial systems. The more limited the access, the fewer chances there are for something to go wrong.
Using role-based access control makes this process easier. By creating access templates based on job roles, you don’t have to manage every user manually. When someone changes departments or leaves the company, their access should be updated or removed immediately. Automating these changes reduces human error and keeps your systems safer without slowing down work.
Use Multi-Factor Authentication (MFA) on All Accounts
Usernames and passwords alone aren’t enough to keep accounts safe. Hackers often steal login details through phishing or data breaches. Multi-Factor Authentication adds a second layer of protection by requiring something the user has, like a phone or security key. Even if someone gets the password, they still can’t log in without the second step.
Applying MFA to all accounts is important, but it’s absolutely critical for privileged accounts. Make it a rule that no one can access high-level systems without passing multi-factor checks. Many tools allow you to use apps, SMS codes, or biometric options. Choose a method that fits your organization, and make sure everyone understands why it’s required.
Regularly Monitor and Audit Account Activity
Keeping an eye on account activity helps you spot problems before they grow. Set up systems to monitor logins, file changes, and unusual behavior. If someone tries to access data they don’t normally use, it could be a sign of an issue. Early detection allows you to act fast and minimize any damage.
Auditing also plays a big role in keeping privileged accounts secure. Review logs regularly to check for policy violations, outdated permissions, or unauthorized access. Use audit results to fine-tune your security plan. Over time, you’ll see patterns that help you prevent future attacks. Audits also help you meet compliance requirements and build trust with clients and stakeholders.
Train Employees on Secure Practices
Technology alone won’t protect your systems. People play a huge role in security, so training your staff is essential. Teach employees how to spot phishing attempts, avoid risky behavior, and report anything suspicious. Make sure they understand the importance of protecting their login information, especially when they have elevated access.
Offer regular refresher sessions, especially when new threats emerge. Include real-life examples to make the lessons stick. Also, explain the purpose behind security tools like PAM and MFA. When users understand why security measures exist, they’re more likely to follow them. Empowered employees become your first line of defense rather than your weakest link.
Remove or Rotate Unused and Shared Accounts
Over time, organizations build up a lot of unused accounts. These may belong to former employees or temporary vendors. If left active, these accounts create security holes that attackers can exploit. Make it a regular habit to remove any account that is no longer in use. Automate this process when possible to keep things efficient.
Shared accounts pose another major risk. If multiple people use the same login, you lose track of who is doing what. This makes it harder to respond to issues or trace malicious actions. Instead, give each person a unique account with specific permissions. Rotate credentials often and never reuse passwords across accounts. These small changes make a big impact.
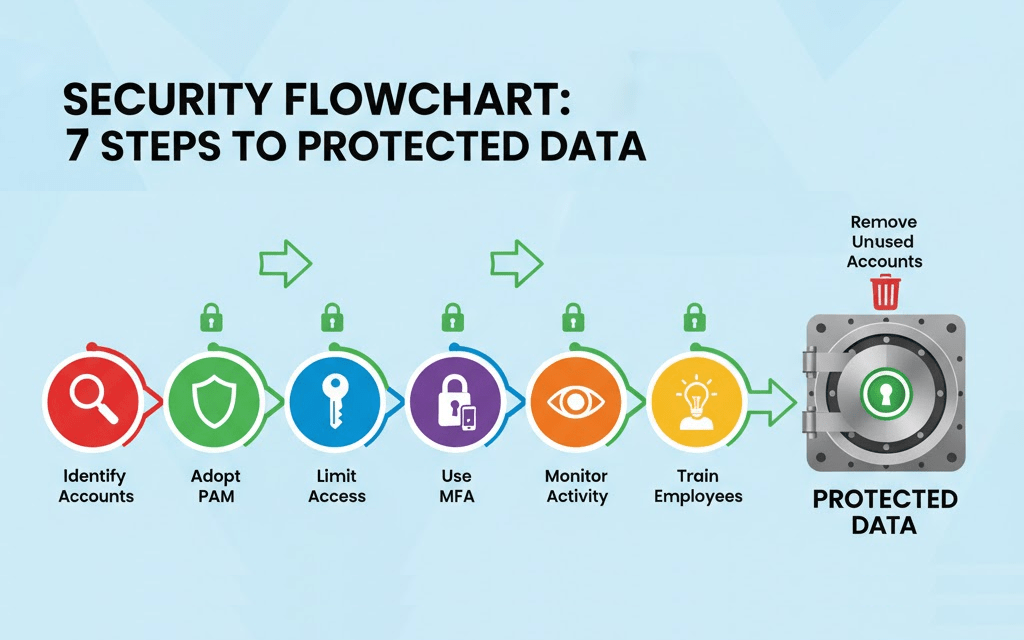
In conclusion, protecting your organization’s most powerful accounts isn’t just an IT task — it’s a business priority. These accounts hold sensitive information and control over critical systems. Taking the time to identify, limit, monitor, and manage privileged access protects not just your data, but your reputation and future. Simple habits like training your team, rotating accounts, and using PAM solutions can go a long way.