Data loss can happen in an instant, whether through a hardware crash, a malware attack, or a simple human mistake. For individuals and businesses alike, the consequences can be severe: lost documents, compromised projects, irreplaceable photos, or prolonged business downtime. Fortunately, most data loss incidents are preventable with a robust backup strategy.
This guide walks you through everything you need to know about backing up your data: why it’s essential, how to do it effectively, and what tools and best practices can help safeguard your digital assets.
The Alarming Reality of Data Loss
To truly grasp the importance of data backup, consider these sobering statistics:
Frequent Occurrences
Data loss isn’t a rare event. Studies consistently show that a significant percentage of individuals and businesses experience data loss each year. Nearly 40% of companies reportedly lose critical data in a cyberattack annually, and more than 1 out of every 100 hard drives fails each year, leading to potential data loss.
Human Error is a Major Culprit
While cyberattacks and hardware failures make headlines, human error remains a leading cause of data loss. From accidental deletions to misconfigured systems, user mistakes contribute to a substantial share of data-related incidents.
The High Cost of Loss for Businesses
The financial consequences of data loss can be severe:
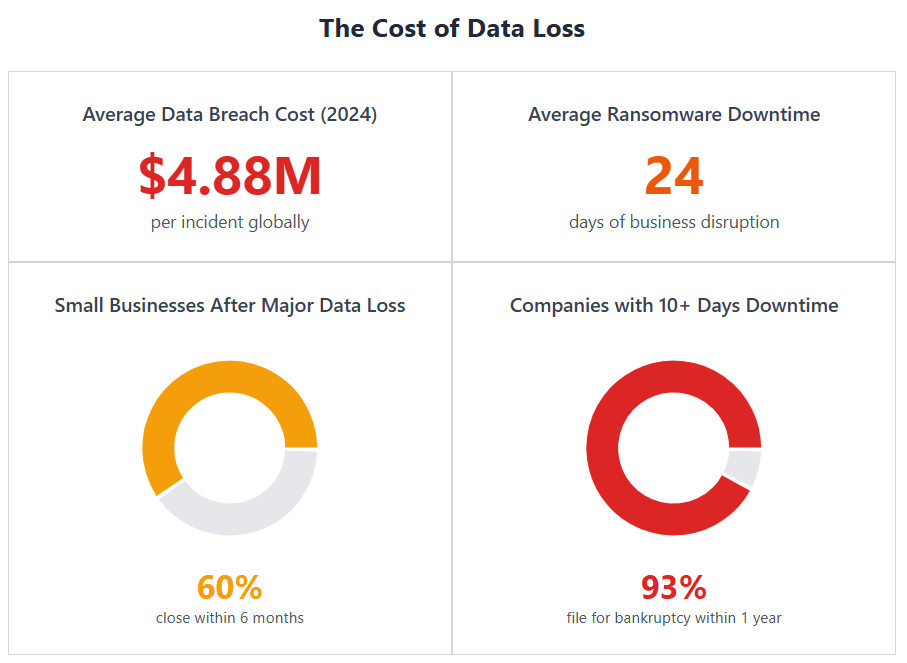
- Rising breach costs: As of 2024, the global average cost of a data breach reached $4.88 million.
- Significant downtime: Ransomware incidents alone can result in an average of 24 days of downtime.
- Reputational damage: Loss of customer trust and a damaged brand image often follow a breach.
- Bankruptcy risk: Up to 60% of small businesses that suffer major data loss close within six months. Additionally, 93% of companies experiencing 10+ days of data center downtime file for bankruptcy within a year.
Personal Impact
For individuals, data loss can be equally devastating. Irreplaceable family photos, creative work, important documents, or personal records lost to theft, corruption, or accidents can cause deep emotional distress or even financial setbacks.
These figures underscore a critical truth: data loss is not a matter of “if,” but “when.” A proactive, layered backup strategy is the most effective way to avoid becoming another statistic.
1. Why Backing Up Data Is Critical
Protection Against Hardware Failures
Even modern storage devices (SSDs, HDDs, USB drives) can fail without warning. A sudden crash could wipe out years of important files. Without a backup, recovery is costly and not always possible.
Defense Against Cyber Threats
Cyberattacks, especially ransomware, are on the rise. Hackers can encrypt your files and demand payment to unlock them. A recent backup allows you to restore your data without succumbing to extortion.
Safeguard Against Human Error
Files get accidentally deleted, overwritten, or formatted. A reliable backup lets you reverse mistakes with minimal disruption.
Resilience to Physical Disasters and Theft
Fires, floods, or stolen devices can destroy your only copy of important data. Backups stored offsite or in the cloud provide a crucial second layer of protection.

2. How to Back Up Your Data Effectively
The 3-2-1 Backup Rule
A foundational strategy for data protection:
- 3 copies of your data (1 primary + 2 backups)
- 2 different types of storage (e.g., external drive + cloud)
- 1 copy stored offsite
This ensures redundancy and protection against multiple types of failure.
Comparison of Backup Methods
| Backup Method | Pros | Cons |
|---|---|---|
| External Hard Drives | Fast, cost-effective, easy to use | Can fail, vulnerable to physical damage |
| Cloud Storage | Accessible anywhere, scalable | Requires internet, subscription-based |
| Network-Attached Storage (NAS) | Ideal for large data and teams | Higher setup cost, technical configuration |
| Automated Backup Software | Hands-off management, customizable | Needs proper setup and testing |
Recommendations by Use Case
- Personal Use: iCloud, Google Drive, Dropbox
- Large Data Sets: Backblaze, external SSDs
- Business & Teams: Synology NAS + cloud sync, Acronis Cyber Protect
3. Step-by-Step Backup Setup
For Beginners
- Pick a backup method: Combine an external drive with a cloud service.
- Use built-in tools:
- macOS: Time Machine
- Windows: File History
- Schedule automatic backups: Set it and forget it.
- Test restores: Periodically restore files to ensure everything works.
For Advanced Users
- Deploy NAS systems with RAID for redundancy.
- Set up versioned, incremental backups using tools like Veeam, Duplicati, or rsync.
- Integrate automated scripts and remote backups for business continuity.
4. Security Best Practices
Encrypt Your Backups
Use encryption to protect sensitive data at rest and in transit. Tools like VeraCrypt or built-in options in backup software can safeguard files from unauthorized access.
Store Backups Securely
- Physically: Use tamper-proof and fire-resistant storage for external drives.
- Digitally: Enable multi-factor authentication for cloud backups and use encrypted volumes.
Manage Passwords Carefully
Use a password manager to generate and store complex passwords. Limit access to backup systems to authorized users only.
5. Creating a Disaster Recovery Plan
Key Components
- Identify Critical Data: Know what must be recovered first.
- Define RTO/RPO:
- RTO (Recovery Time Objective): How fast can you get back online?
- RPO (Recovery Point Objective): How much data loss is acceptable?
- Assign Roles and Responsibilities: Designate who does what in an emergency.
Test the Plan
- Simulate data loss scenarios regularly.
- Review the time and effectiveness of your recovery process.
- Update the plan as your systems and data evolve.
6. Common Mistakes to Avoid
- Incomplete Backups: Don’t forget system files, application data, and configurations.
- Infrequent Backups: Set schedules that match the frequency of data changes.
- Neglecting Updates: Keep your backup tools and storage devices updated.
- No Redundancy: Don’t rely on just one device or method.
7. Backup Strategies for Different Devices
Computers
- Windows: File History, Acronis, Macrium Reflect
- macOS: Time Machine, Carbon Copy Cloner
- Linux: rsync, Déjà Dup, Timeshift
Mobile Devices
- iOS: iCloud or iTunes backups
- Android: Google One, Samsung Cloud, local transfers
Servers & Databases
- Use snapshot tools, database dumps (e.g.,
mysqldump), or enterprise solutions like Veeam or Acronis. - Backups should be automated, encrypted, and tested frequently.
8. Automating Your Backups
Recommended Tools
- Mac: Time Machine, Carbon Copy Cloner
- Windows: Acronis Cyber Protect, Macrium Reflect
- Cross-platform: Duplicati, Backblaze, AOMEI Backupper
Scheduling Backups
- Use built-in scheduling features or OS-level schedulers (e.g., Task Scheduler, cron).
- For mission-critical systems, use hourly or real-time syncing.
Monitoring
- Enable email or app alerts for failed backups.
- Use dashboards to track backup status and history.
9. Examples
🥳 Success Story
A small e-commerce company using a combination of NAS and cloud backups was hit by ransomware. Their backup strategy allowed them to recover operations within hours without paying the ransom.
😓Cautionary Tale
A wedding photographer lost all client photos when their only external drive was stolen. No cloud backup existed, leading to legal issues and reputational damage.
10. Glossary of Backup Terms
- Incremental Backup: Backs up only changes since the last backup
- Full Backup: A complete copy of all selected data
- RTO: Maximum acceptable downtime after an incident
- RPO: Maximum acceptable data loss in time
- NAS: Network-Attached Storage — a private, connected backup device
- Image Backup: A full copy of your system, apps, and files
- End-to-End Encryption: Data is encrypted before transmission and remains encrypted until recovery
11. Resources and Further Reading
📖 Books
- Backup & Recovery by W. Curtis Preston
- The Disaster Recovery Handbook by Michael Wallace and Lawrence Webber
🔗Online Courses
- LinkedIn Learning: Learning Backup and Recovery
- Coursera: IT Infrastructure and Data Management Courses
🧑🤝🧑Communities
- Reddit: r/DataHoarder
- Spiceworks: Backup & Recovery Forum
- LinkedIn: Data Security & Recovery Groups
Conclusion
Safeguarding your data is a critical responsibility. Whether preserving family photos or vital business files, a well-crafted backup strategy ensures protection and peace of mind. Implement the 3-2-1 rule, choose effective tools, automate processes, and develop a recovery plan to build digital resilience.












